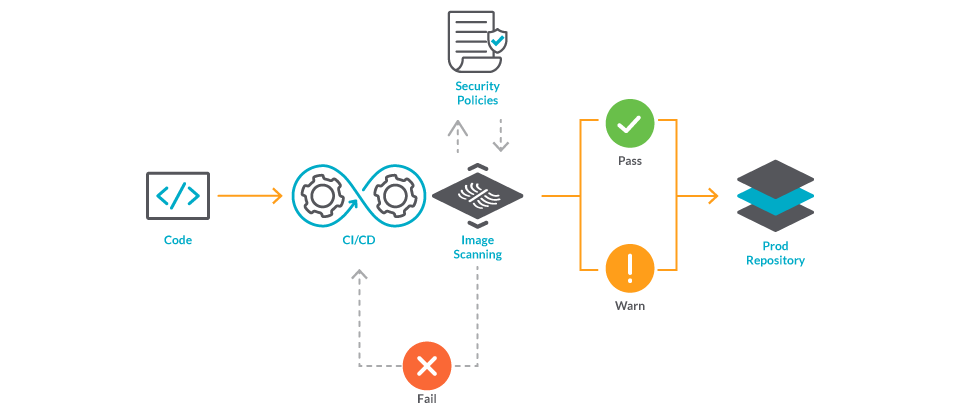
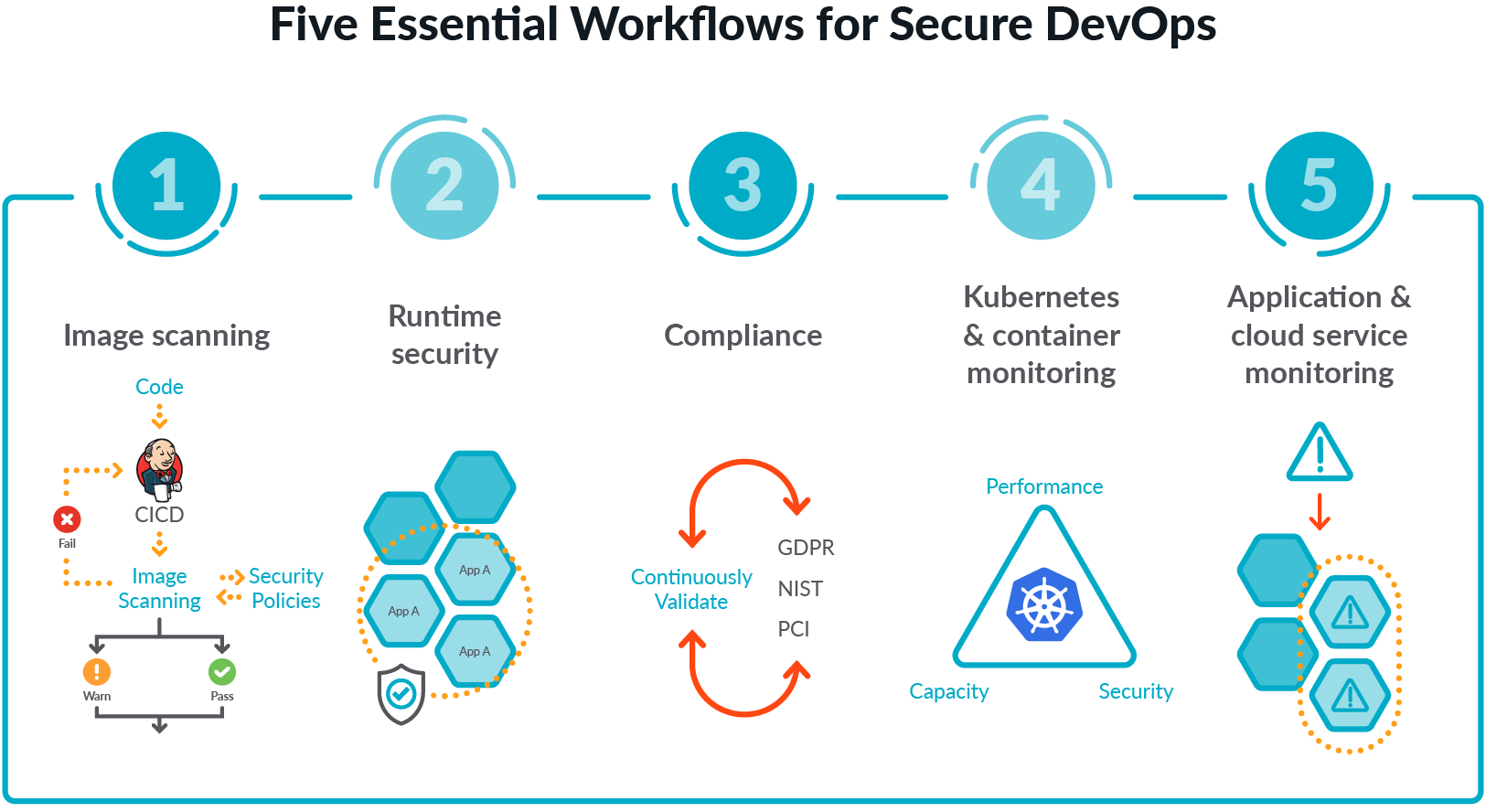
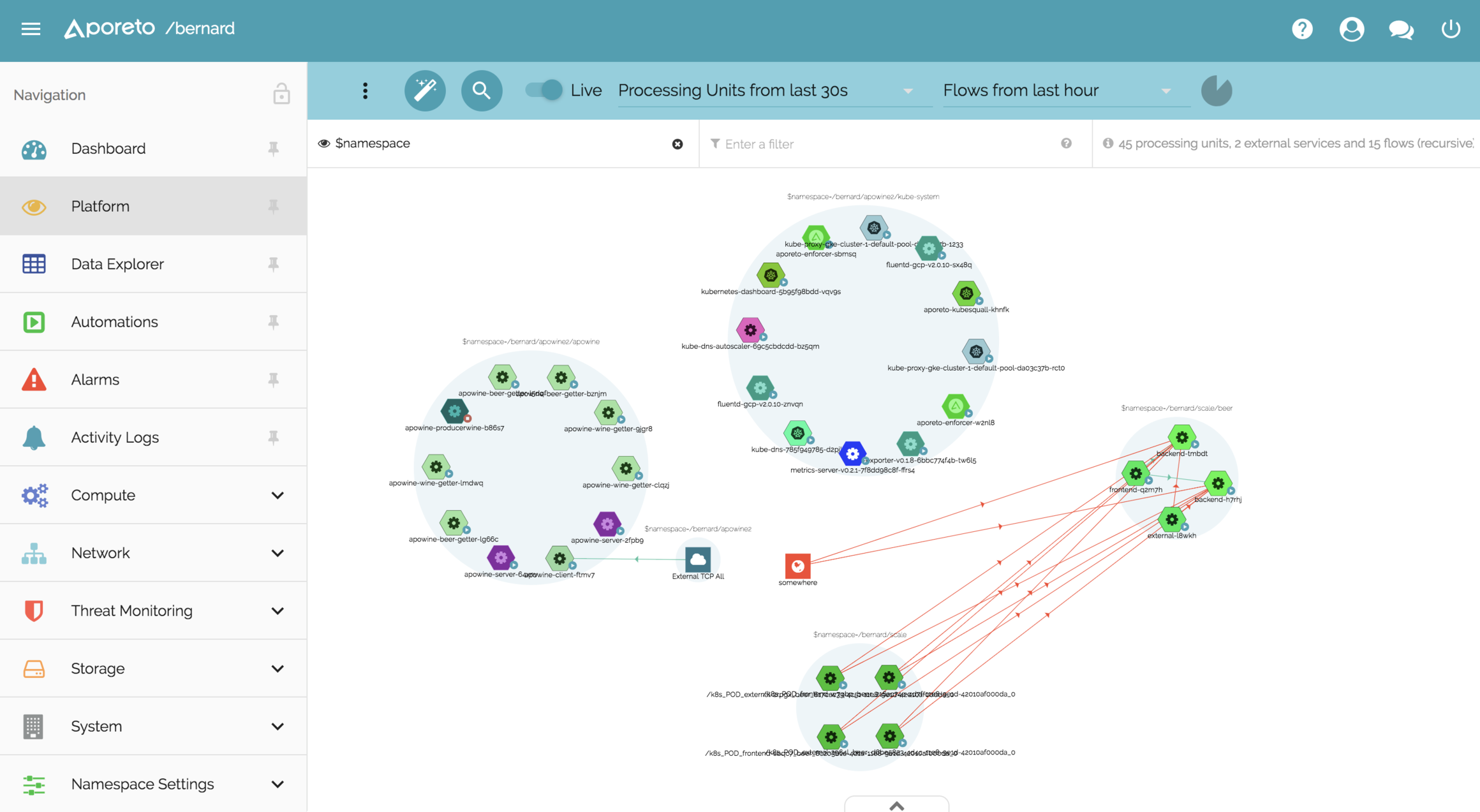
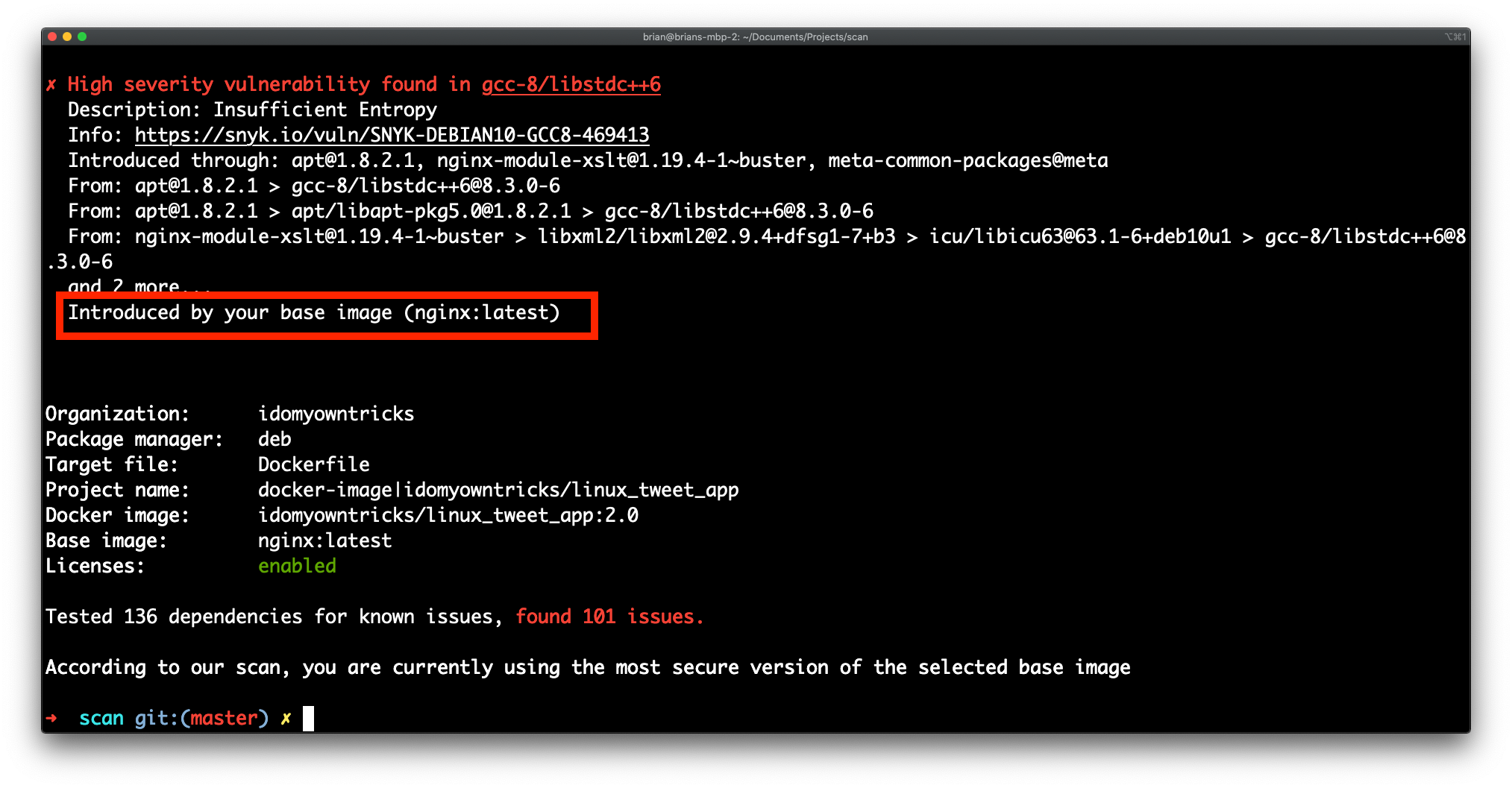
Guard against security vulnerabilities in your software supply chain with Container Registry vulnerability scanning | Google Cloud Blog

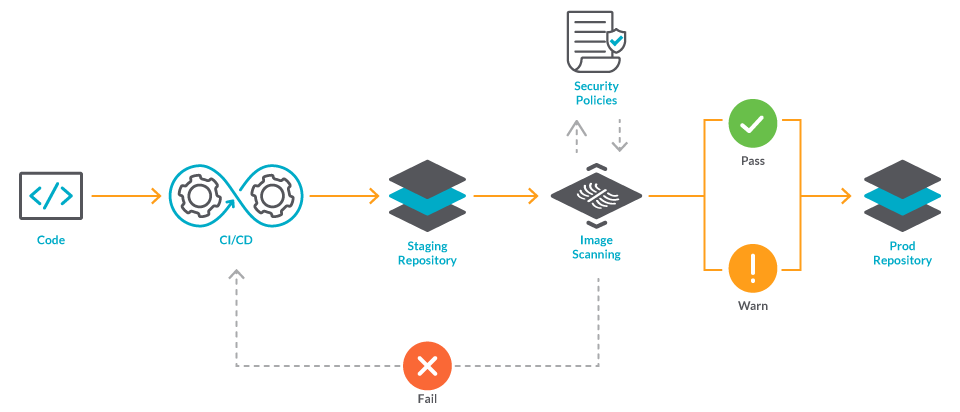
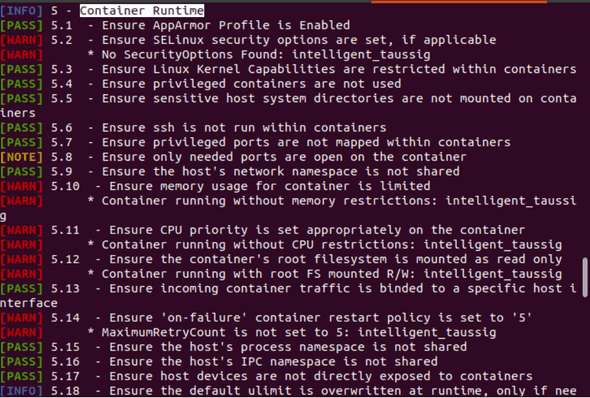
How to build a CI/CD pipeline for container vulnerability scanning with Trivy and AWS Security Hub | AWS Security Blog